Introduction to AWS CloudFormation Guard
AWS CloudFormation Guard is an open-source command line interface (CLI) that helps enterprises keep AWS infrastructure and application resources in compliance with the company policy guidelines. It provides compliance administrators with a simple, policy-as-code language to define rules that can check for both required and prohibited resource configurations. It enables developers to validate their CloudFormation templates against those rules.
In this exercise, you learn using AWS CloudFormation Guard.
Step1: Pre-Requisite
You need to have an AWS account with administrative access to complete the exercise. If you don’t have an AWS account, kindly use the link to create free trial account for AWS.
Step2: Create Cloud9 Environment
You use an Amazon Cloud9 environment to use AWS CloudFormation Guard with CloudFormation Templates.
-
Login to AWS Management Console and choose Ireland as the region.
-
Goto the AWS Cloud9 console and click on the Create environment button.
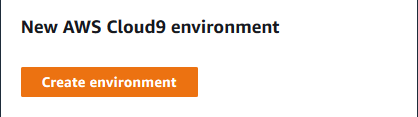
-
On the next screen, enter dojoenvironment as the name and click on the Next step button.
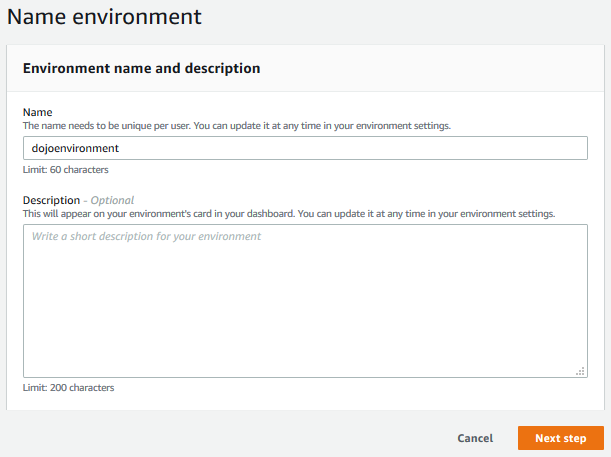
-
On the next screen, select Environment type as Create a new EC2 instance for environment (direct access). Select Instance type as t2.micro (1 GiB RAM + 1 vCPU). Select Amazon Linux 2 for the Platform. Keep rest of the fields with the default values and click on the Next step button.
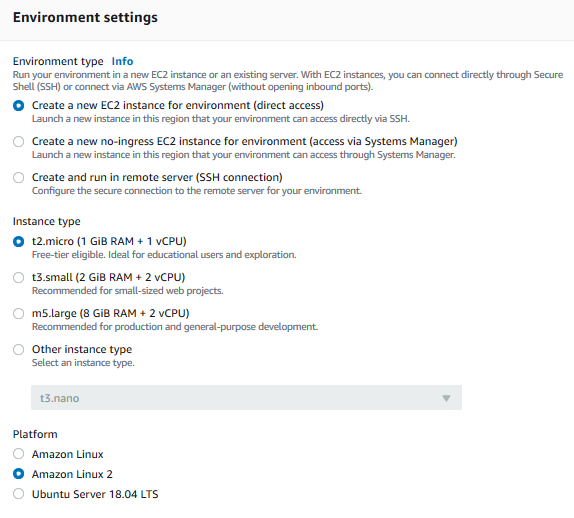
-
On the next screen, click on the Create environment button.
-
It will take couple of minutes to create the environment. In the next step, you will deploy Amazon CloudFormation Guard in the environment.
Step3: Deploy Amazon CloudFormation Guard
You deploy Amazon CloudFormation Guard in the Cloud9 environment in order to use it.
-
In the AWS Cloud9 console, run the command wget https://github.com/aws-cloudformation/cloudformation-guard/releases/download/1.0.0/cfn-guard-linux-1.0.0.tar.gz to download the release package of CloudFormation Guard for the Linux environment. It is recommended to use the link to find the latest release.
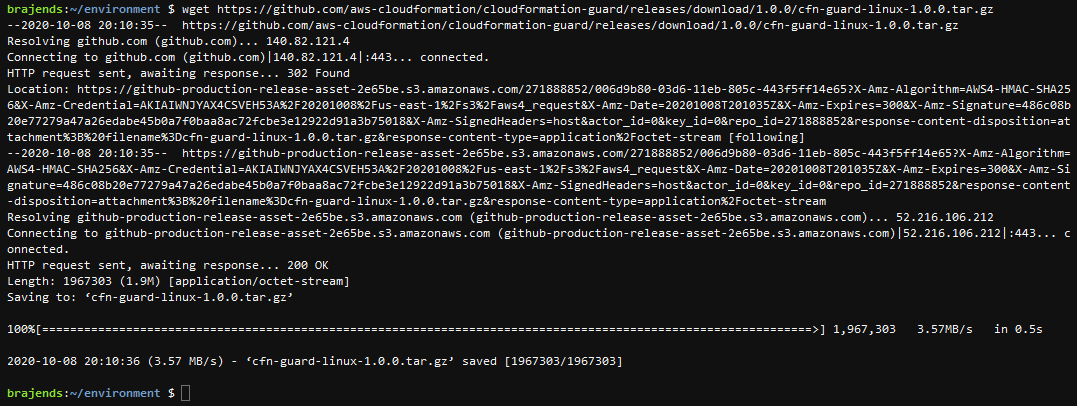
-
Run the command tar -xvf cfn-guard-linux-1.0.0.tar.gz to unzip the release package for CloudFormation Guard. It will unzip the package in the cfn-guard-linux folder. You can see cfn-guard command under cfn-guard-linux folder which is used to check compliance on the CloudFormation templates.
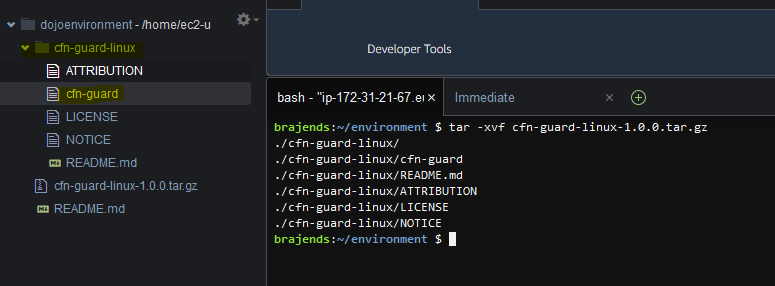
-
CloudFormation Guard is ready. It is time to check for compliance in CloudFormation Templates.
Step4: Using CloudFormation Guard
In this step, you use CloudFormation Guard to perform rule based compliance check on CloudFormation Templates.
-
In Cloud9 environment, use New File menu option under File to create a new file dojotemplate.yaml. Copy-paste the following CloudFormation Template into it. When performing copy-paste, take care of the indentation as indentation matters in YAML based template.
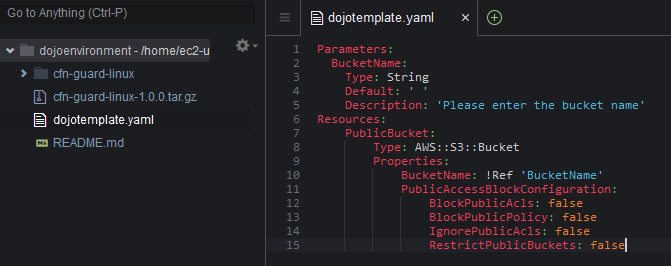
Parameters: BucketName: Type: String Default: ' ' Description: 'Please enter the bucket name' Resources: PublicBucket: Type: AWS::S3::Bucket Properties: BucketName: !Ref 'BucketName' PublicAccessBlockConfiguration: BlockPublicAcls: false BlockPublicPolicy: false IgnorePublicAcls: false RestrictPublicBuckets: false`
-
The template is very simple. It is creating a public Amazon S3 bucket. You now want to create a rule which checks for public bucket creation and raises alert if the template has configuration for public bucket creation.
-
So, how does the rule configuration format look like? Run the command ./cfn-guard-linux/cfn-guard rulegen ./dojotemplate.yaml to print the configuration format of the rules.
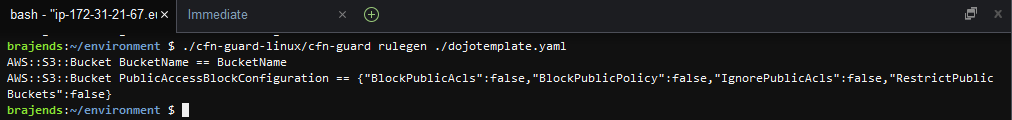
-
Let’s pipe these rule configuration format into a file so that you can configure it to check for public bucket creation. Run the command ./cfn-guard-linux/cfn-guard rulegen ./dojotemplate.yaml > dojo.ruleset to create a ruleset file dojo.ruleset. You can see the file created in the environment.
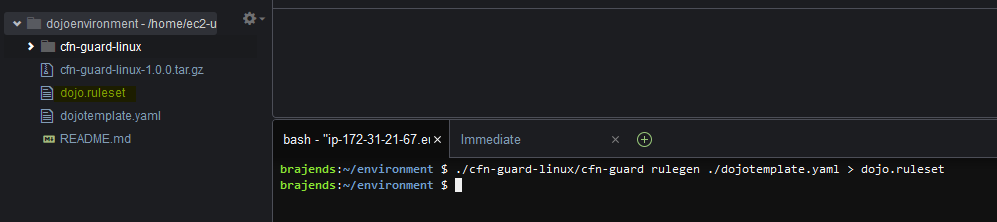
-
Open the dojo.ruleset file. Remove AWS::S3::Bucket BucketName == BucketName line as you don’t want any rule on the bucket name. Update the second line as following -
AWS::S3::Bucket PublicAccessBlockConfiguration == {"BlockPublicAcls":true,"BlockPublicPolicy":true,"IgnorePublicAcls":true,"RestrictPublicBuckets":true}`
-
Save the dojo.ruleset file. The saved file should look like the following.
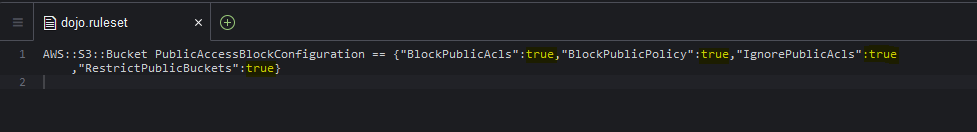
-
Basically, you are setting the desired configuration in the ruleset for the CloudFormation Template; which in this case is that the bucket should not be public. If a CloudFormation Template has configuration to create public bucket, CloudFormation Guard would raise alert about. Run the ./cfn-guard-linux/cfn-guard check -t ./dojotemplate.yaml -r dojo.ruleset to check compliance of dojotemplate.yaml against the dojo.ruleset. You can see one alert stating not using permitted value for PublicAccessBlockConfiguration.
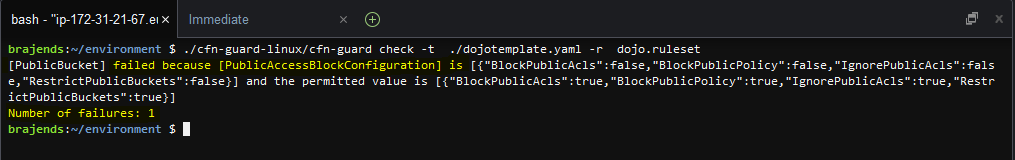
-
Let’s update and save dojotemplate.yaml as the following to make it compliant with the ruleset.
Parameters: BucketName: Type: String Default: ' ' Description: 'Please enter the bucket name' Resources: PublicBucket: Type: AWS::S3::Bucket Properties: BucketName: !Ref 'BucketName' PublicAccessBlockConfiguration: BlockPublicAcls: true BlockPublicPolicy: true IgnorePublicAcls: true RestrictPublicBuckets: true`
-
Run the ./cfn-guard-linux/cfn-guard check -t ./dojotemplate.yaml -r dojo.ruleset again. This time, you get no failure message because the template is now compliant with the rules.
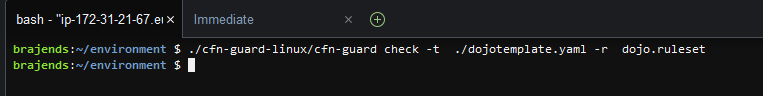
-
This finishes the exercise. Goto the next step to clean-up the resources so that you don’t incur any cost after the exercise.
Step5: Clean up
Delete the dojoenvironment Cloud9 Environment.
Thanks and hope you enjoyed the exercise.

