Let’s create a Security Group which is used by the MySQL Database Instance and AWS Glue Connection. You also create S3 bucket which is used as the destination location for the Glue job.
-
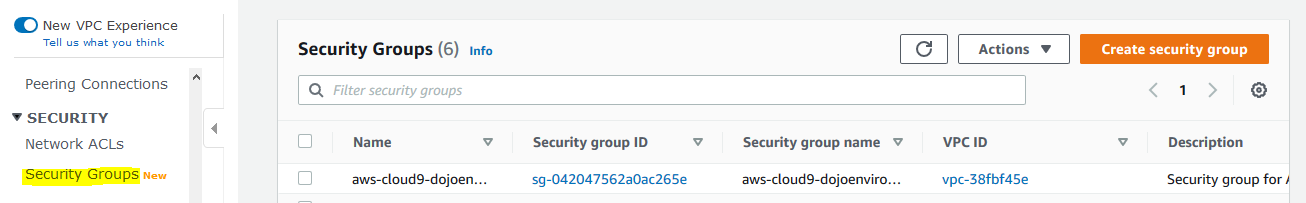
Goto VPC Management Console. Click on the Security Groups menu in the left and then click on the Create security group button.
-
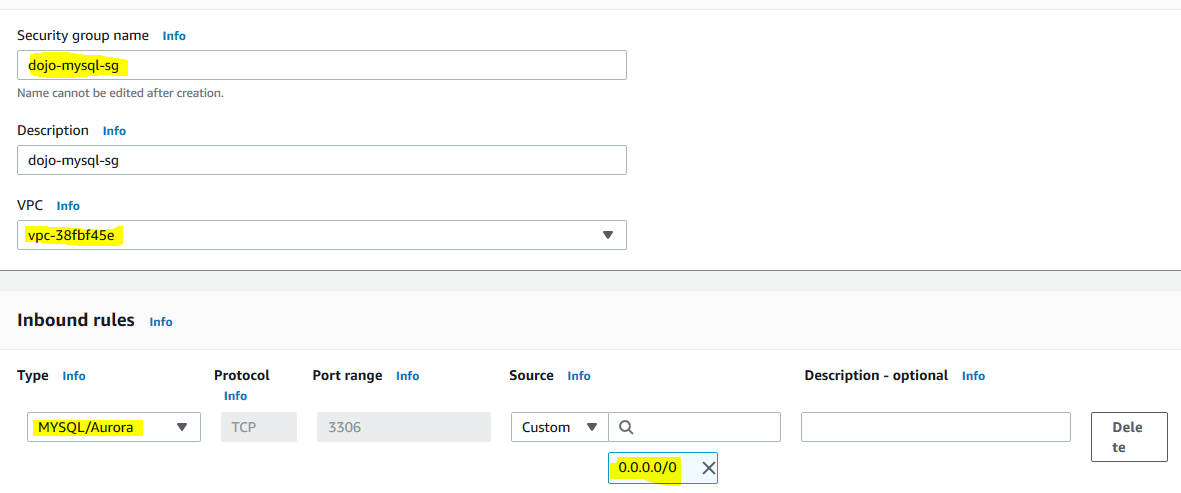
On the next screen, type in dojo-mysql-sg for the security group name and the description fields. Select the default VPC for the VPC field. Create inbound rule for MYSQL/Aurora for Source = 0.0.0.0/0. Keep rest of the configuration to the default. Click on the Create security group button.
-
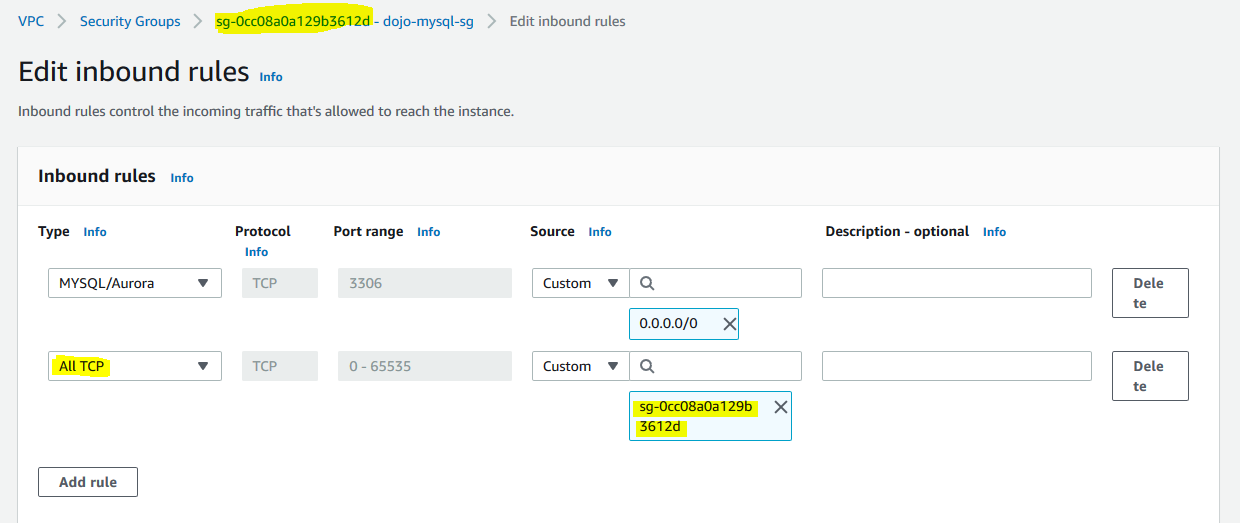
The security group is created in no time. Once the security group is created, update the inbound rule to allow All TCP type communication from the security group itself (self-referencing) as shown below.
-
You then create a S3 bucket with the name dojo-target-bucket which will work as the destination for the Glue Job. If the bucket name is not available, create with a name which is available.

-
The Next step is to launch Aurora / MySQL database instance.
